Neural Inverse Private Limited | Building the First Enterprise On-Chain IDE
The Origin of Neural Inverse
Neural Inverse was founded by Manipal student Sanjay Senthilkumar after his research revealed a critical flaw: the multi-billion dollar on-chain industry runs on inadequate, high-risk development tools. The company was incorporated in India on November 11, 2024, to build the professional, intelligent solutions this high-stakes environment demands.
What Problem Neural Inverse Solving
Enterprises demand absolute control over immutable, high-stakes contracts, yet their developers build in a broken environment lacking enforceable compliance and effective tooling. This fundamental disconnect is the direct source of the preventable, multi-billion dollar errors that kill companies and stifle innovation.
A single problem is faced by Developer and Enterprise
Dev
Developers are required to create high-stakes contracts in an environment lacking effective tools and debuggers, with N Number Unknown plugins. This leads to vulnerabilities and development flaws in Contracts, resulting in significant losses for enterprises.
Enterprise
Enterprises demand high security and control, yet developers, often inexperienced, must use inadequate tools lacking compliance checks no control over their Product development, leading to costly errors at best and company closure at Worst due to product unusability and Trust.
Every Data Point Points to One Core Problem
Market Losess

Drawing on deep experience in both high-velocity engineering and high-stakes enterprise security, we've built the dedicated on- chain development environment where a professional, intuitive workflow and non-negotiable, enforceable compliance are one and the Same, empowering teams to build valuable assets with both speed and institutional-grade policy via one Solution.
For Enterprise | Governance & Enterprise Layer
For Developers | Efficiency & Productivity Layer
Our Innovation
Policy-as-Code
AI embeds dynamic security rules in dev cycles, eliminating 38% DeFi audit failures for inevitable compliance in immutable contract deployments.
AI Co-pilot
Neural Inverse's AI fine tuned models automate code orchestration, predicting flaws via Agents modeling to cut 33% human-error losses in hacks.
Complex Systems
Our system, built with intricate algorithms, streamlines on-chain dev, ensuring precise contract creation and deployment with 40% efficiency gains.
Interactive Debuggers
Neural Inverse’s debuggers dissect code in real-time within the IDE, eliminating bugs like Nomad’s $190M fiasco—pure, no-nonsense precision.






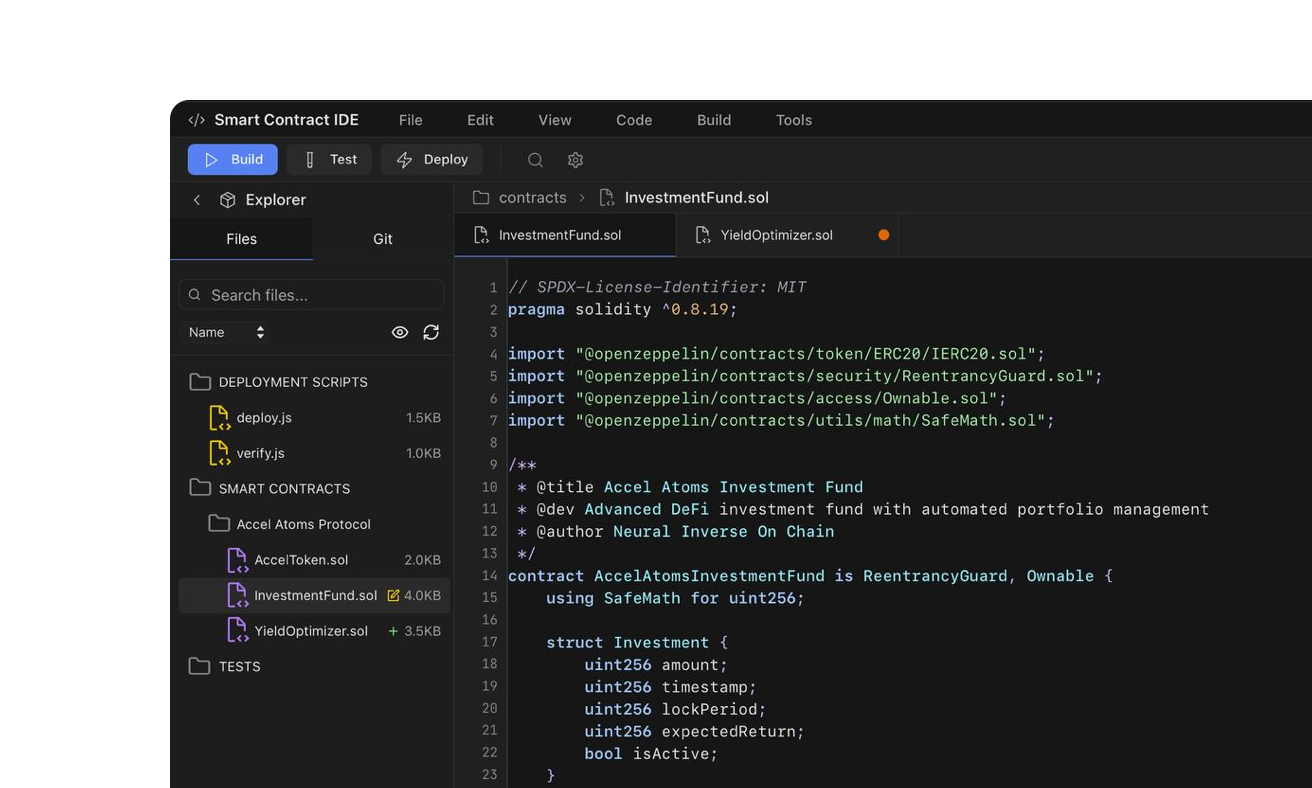
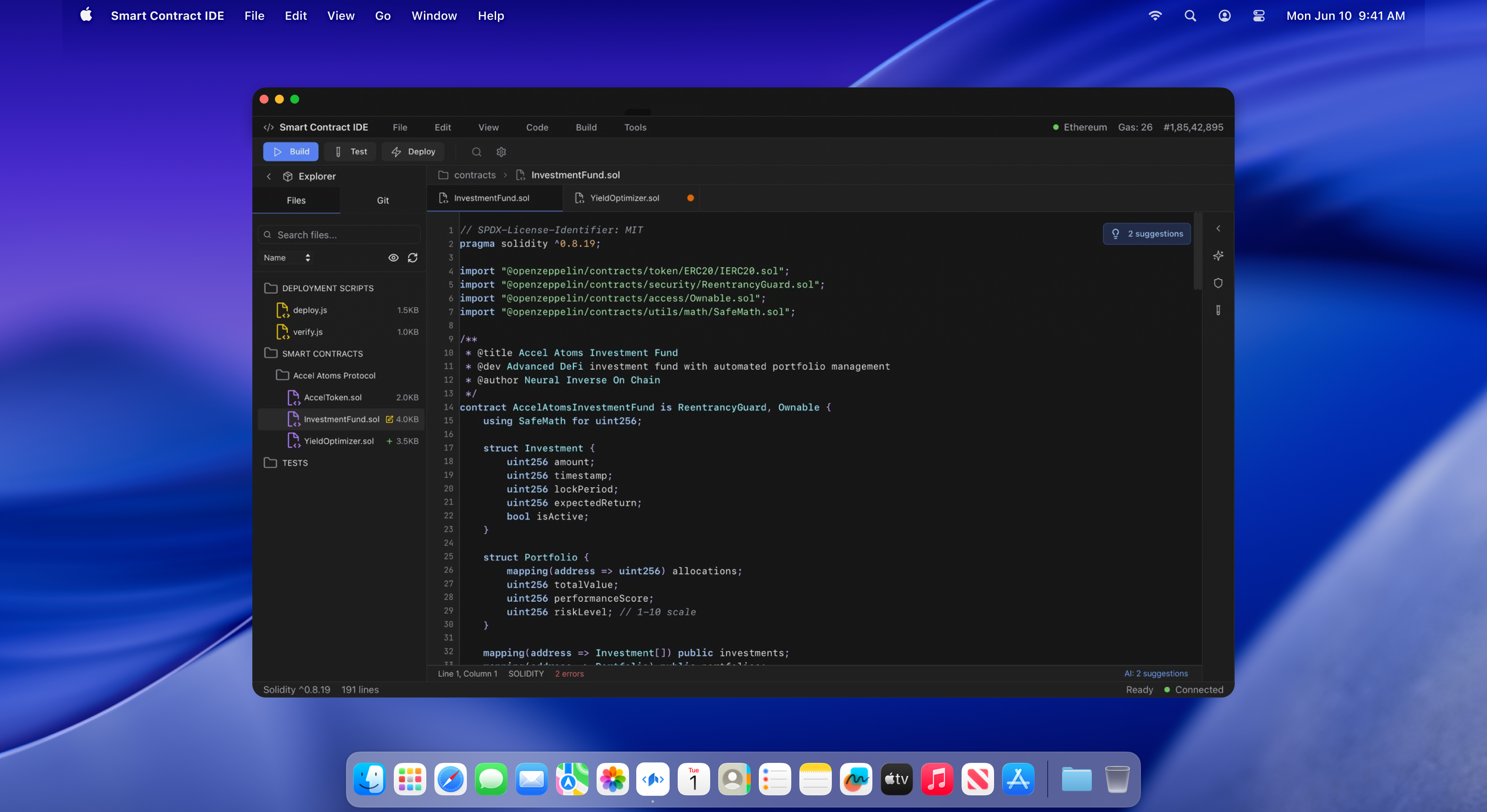
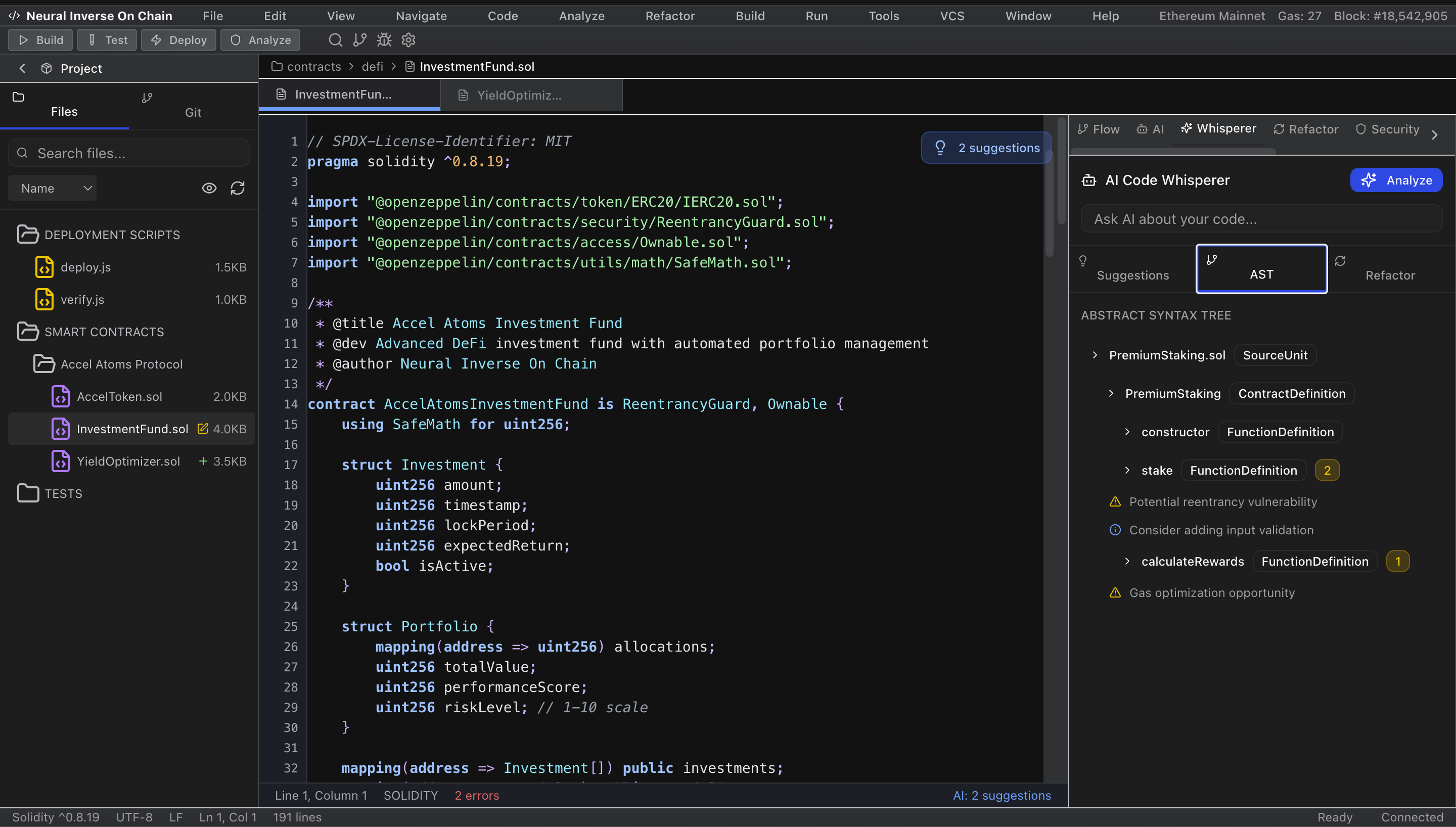
Competitive analysis
.png)
